
Cybersecurity Threats in 2025: What Businesses Must Do to Stay Secure
The Cyber Threat Landscape Is Changing—Fast.
As we move through 2025, cyber threats are growing more sophisticated, and the old ways of defending your business aren’t enough anymore. Cybercriminals are using AI, exploiting supply chains, and targeting cloud environments at an unprecedented scale. Whether you’re running a startup or a global team, cybersecurity is no longer optional—it’s essential for survival, growth, and trust.
This guide breaks down 2025’s top cybersecurity threats and gives you clear steps to protect your business. If you’re ready to secure your future, read on.
Top 5 Cybersecurity Threats to Watch in 2025 (and How to Defend Against Them)
1. AI-Powered Attacks: Smarter, Faster, Harder to Spot
AI isn’t just helping businesses innovate—it’s giving cybercriminals new weapons.
•Hyper-Realistic Phishing Emails created using AI language models are harder to spot than ever.
•Adaptive Malware changes its code in real-time, evading traditional antivirus and security systems.
•Deepfake Technology is enabling cybercriminals to impersonate executives and trick employees into sending payments or sensitive data.
How to Protect Your Business:
• Invest in AI-driven threat detection and response platforms.
•Train employees regularly on how to spot sophisticated phishing and impersonation attempts.
•Implement multi-step verification for any high-stakes decisions or financial transactions.
2. Ransomware-as-a-Service (RaaS): Cybercrime on Subscription
Ransomware attacks are booming—and you no longer need to be a hacker to launch one. Criminal groups are renting out their ransomware like software subscriptions.
•Double and Triple Extortion attacks are becoming the norm: encrypting your data, stealing it, and threatening public exposure or DDoS attacks unless you pay up.
•Cloud Ransomware is on the rise, targeting businesses that rely on cloud services.
How to Protect Your Business:
•Deploy multi-layered security defenses, including endpoint protection and regular vulnerability scans.
•Run frequent backups, test them, and ensure they are isolated from your main network.
•Consider Managed Detection and Response (MDR) services for 24/7 monitoring and rapid response.
3. Supply Chain Attacks: One Weak Link, Big Consequences
Your vendors and suppliers can become the back door into your systems.
•Software Supply Chain Hacks (like the SolarWinds attack) can impact thousands of businesses at once.
•Third-Party Credential Compromises give hackers privileged access to your environment.
How to Protect Your Business:
• Conduct vendor security assessments regularly.
•Enforce Zero Trust Architecture (ZTA)—trust no one, verify everything.
•Limit vendor access to only what they need, and review it often.
4. Human Hacking: Social Engineering Gets Personal
Despite the technology, people remain the easiest targets.
•Business Email Compromise (BEC) scams are responsible for billions in losses worldwide.
•Vishing (voice phishing) and smishing (SMS phishing) attacks are growing rapidly as people become numb to email warnings.
How to Protect Your Business:
•Train your entire team in cybersecurity awareness, focusing on spotting and reporting suspicious activity.
•Implement multi-factor authentication (MFA) across all systems.
•Create clear internal processes for verifying unusual or high-risk requests.
5. Cloud Vulnerabilities: Misconfigurations and Credential Theft
As businesses move more operations to the cloud, missteps are common.
•Misconfigured Cloud Environments can leave sensitive data exposed to the public internet.
•Stolen Credentials can give hackers full access to cloud platforms in minutes.
How to Protect Your Business:
• Perform regular cloud security audits.
•Use Cloud Access Security Brokers (CASBs) to monitor and control cloud traffic.
•Enforce strong Identity and Access Management (IAM) policies, including privileged access controls.
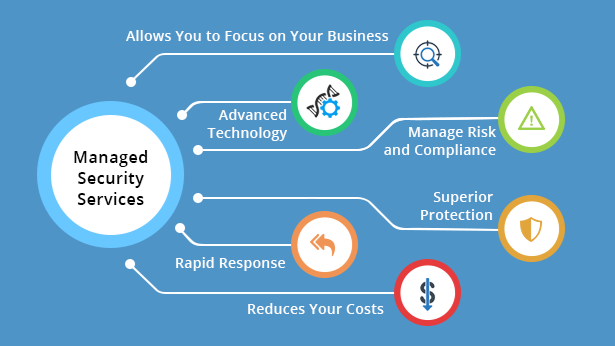
Why Managed Security Services Are Essential in 2025
Keeping up with cyber threats is a full-time job—and you already have a business to run. Managed Security Services (MSS) like those offered by Chibitek give you peace of mind, knowing that experts are monitoring your systems 24/7.
Here’s What You Get with Chibitek MSS:
• Proactive Threat Detection & Response
• Security Awareness Training for Your Team
• Cloud & Network Security Audits
• Compliance Support (HIPAA, GDPR, etc.)
•Rapid Incident Response in the event of a breach
Final Word: Cybersecurity Isn’t Just IT—It’s Business Survival
2025 is the year to stop playing defense and start building a proactive, resilient cybersecurity strategy.
Businesses that prioritize security aren’t just protecting their data—they’re protecting their reputation, their customers, and their future.
Need help building your cybersecurity game plan?
Reach out to Chibitek today for a free consultation.
Let’s make IT effortless—so you can disrupt, create, and grow.











