Cyber threats aren’t slowing down—they’re getting smarter, faster, and harder to track. In a recent joint advisory issued by the National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), Canadian Centre for Cyber Security (CCCS), and New Zealand National Cyber Security Centre (NCSC-NZ), a specific tactic known as Fast Flux was identified as a growing national security concern. At Chibitek, we want to break this down for you and explain why it matters—even if you’re not running a government agency or a Fortune 500 company.
Understanding Fast Flux: Single vs. Double Flux Techniques
To better understand why Fast Flux poses such a significant cybersecurity threat, it’s important to explore how it actually works. Malicious cyber actors typically deploy two main variants of Fast Flux, each designed to evade detection and maintain the availability of malicious infrastructure.
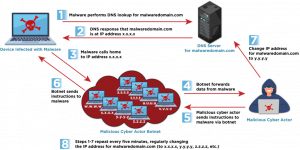
🔄 Single Flux: One Domain, Many IPs
In a single flux configuration, a single domain name is rapidly rotated across multiple IP addresses. Each time a user (or system) attempts to reach the domain, the DNS response returns a different IP address from a pool of compromised hosts—often part of a botnet.
If one IP is blocked or taken down, the domain remains reachable through others in the pool. This approach allows threat actors to maintain persistence while dodging traditional security measures like IP blacklisting.
Figure 1: A visual example of single flux, where one domain resolves to many rotating IPs.
👉 Note: While this tactic is often associated with malicious activity, similar behavior can occur in legitimate systems like content delivery networks (CDNs) or global load balancers for performance reasons. The key difference lies in intent and context.
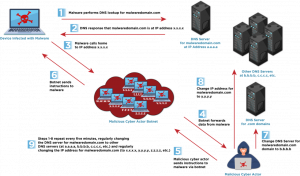
Double Flux: Obscuring the DNS Infrastructure Itself
Double flux takes this strategy even further. In addition to rotating the domain’s IP addresses, the DNS name servers responsible for resolving that domain also change frequently. This adds another layer of obfuscation and redundancy.
Attackers use dynamic updates to both NS (Name Server) and CNAME (Canonical Name) records to achieve this, making it even harder for defenders to trace or block the infrastructure effectively.
Figure 2: A more advanced variant—double flux—where both IP addresses and name servers constantly rotate.
Why Fast Flux Is So Dangerous
Both techniques rely heavily on a botnet of compromised devices, which act as intermediaries or relays to make tracing and blocking even more complex. These compromised devices are often part of Bulletproof Hosting (BPH) services—providers that host malicious content while ignoring takedown notices or law enforcement requests.
Real-world examples of Fast Flux in action include:
•Ransomware campaigns such as Hive and Nefilim.
•Nation-state groups like Gamaredon using Fast Flux to bypass IP blocking.
•Criminal infrastructure hosted by BPH services that offer Fast Flux as a feature.
Key Advantages for Threat Actors
The reason Fast Flux is so widely used by cybercriminals boils down to three main benefits:
•Resilience: The ever-changing IPs make it extremely difficult for law enforcement to keep up and shut them down.
•Ineffective Blocking: By the time a malicious IP is blacklisted, it’s no longer in use.
•Anonymity: The continuous flux of DNS records complicates attribution and takedown efforts.
How Chibitek Is Protecting Our Clients
At Chibitek, we’ve always believed that cybersecurity isn’t an afterthought—it’s the foundation.
Here’s how we’re proactively defending against Fast Flux and similar threats:
✅ Secure Edge DNS Filtering
We use managed DNS filtering to block access to known malicious domains before they even reach your network.
✅ 24x7 Endpoint Detection & Response (EDR)
Our clients are protected with industry-leading EDR tools like Datto EDR and Bitdefender, which detect and isolate threats in real-time.
✅ RocketCyber SOC Integration
All suspicious activity is monitored by a Security Operations Center (SOC). Any anomalies—including DNS flux behavior—are investigated and remediated.
✅ Dark Web & Domain Monitoring
Clients on our 365 Pro Plan receive ongoing domain-based threat intel and dark web surveillance to catch exposure before it becomes a crisis.
✅ Quarterly Vulnerability Scans
Regular scans help us catch weaknesses that attackers would exploit in a Fast Flux campaign or related attack vector.
What You Can Do Now
•Ask your current provider if they monitor for Fast Flux DNS activity.
•Audit your DNS configuration—especially if you self-manage.
•Consider upgrading to a security-first IT stack that includes DNS protection, EDR, and SOC oversight.
At Chibitek, we understand that your business isn’t just about uptime—it’s about trust, continuity, and resilience. As cyber threats grow more advanced, your protection should too.
If you’re unsure where your current IT stack stands in the face of threats like Fast Flux, let’s talk.
We’re not just your MSP—we’re your cybersecurity partner.
📬 Contact us today or email hello@chibitek.com for a complimentary threat readiness check.
We Make IT Effortless, So You Can Disrupt, Create, and Grow